There are two previous posts about this program that go into greater detail on the specifics. there is a breif recap in this post.
Before I take a break with this project, the first one I’ve ever written about, I wanted to close out with a dunk.
Exposition
Now that monetization is the primary goal of social media companies, we see opportunists wanting to fill an artificial vacuum in the social media space with their own formulated mechanic. The rush is here, and it isn’t for gold. Instead, California is a place filled with the opportunity of meeting new people, a service sold to the masses as a product. While not a bad thing on it’s own, it is better if there were more awareness behind a more holistic conception of companies like Tinder.
Did you know that Match.com owns Tinder? It is very telling that they have skin in the game on both ends. I do mean that literally. It is well known that Match is primarily used to find possible partners for relationships. Tinder, under the guise of being a dating app, launched with success among younger users. Now that their campaign focuses on staying single, what is the implied purpose of their service? It’s simple. Tinder is now the perfect window shopping hookup scheme.
There is the small amount of dignity to be found in pivoting to the unabashed hookup service many of its users were already familiar with.
I’ve decided to target Tinder because I find the youth capturing pretty shallow. Acquiring a young user base, and then transitioning into a service that is now selling sex, warrants heavy scrutinization.
Ease of Use
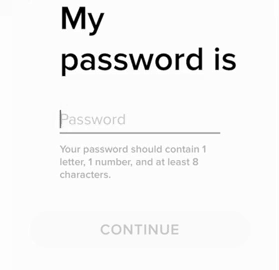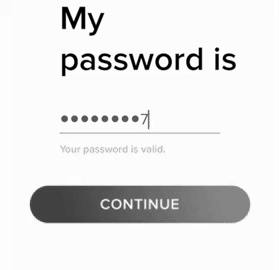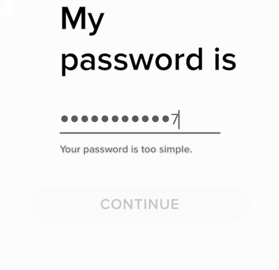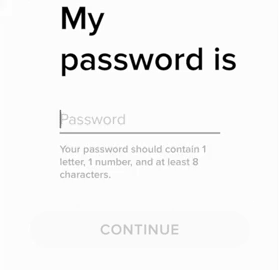
A great deal of people make the error in assuming that the security systems of household names in technology and software correlate to their brand awareness. The security theater Tinder puts on for their customers starts before they even have their account, on the password creation page.
There’s also the issues of maintaining account authenticity. Within the first hour of using a linked Facebook account to run the bot program I had written, it was flagged for suspicious activity. No matter, simply download a free trial for a burner text address, and use that number to authorize a new Tinder account. As of yet, I have run into zero issues using this method.
After I created the account with the burner number, I could use a program that would let my bot authenticate without the Tinder app, and start talking to their servers directly. All kinds of data is immediately vulnerable: distance from origin, Instagram account, pictures, and age to name a few.
Program Overview
The main attack point of my program is through the pictures. Users upload them to Tinder in order to generate appeal for their profile. Sometimes they use photos from other social media accounts, which can be calculated with this program. This bot also uses facial recognition from the supplied photos in order to determine a match. By supplying photos from a searchable social media platform, you can in effect, “search” for certain users on Tinder, which is conventionally unsearchable. I can’t look up a certain account on Tinder.
Tinder does have some restrictions on the rate limit for requests to their servers. I can only access a certain number of users so many times per hour. My idea to compensate for this rate limit was to add more reference photos to the program. This increases both processing time and accuracy. A “lose-win”.
I also found out that Tinder only lets you have a certain amount of likes. In order to get more, you have to purchase a subscription to a premium account. Funny enough, they grant you unlimited dislikes. The drawback with this, is that you start to see disliked users multiple times. I combatted this by checking the URL address of an account’s first photo, a property I saved for every account the Tinder servers sent to me. If I already had that link, I would skip the account.
The Big Test
Obviously, I didn’t want to pick a random Instagram account, unsure if it would actually have a user who also had a Tinder profile. That wouldn’t make for the best thing to write about. I opted to simulate the appropriate conditions for the program to work under the actual circumstances.
On an independent Tinder account on my phone, I swiped until I found a user who had linked their Instagram profile. For this Tinder account’s settings, I used the “suggested users” filter, with a radius of 10km in a specific area, seen in green on this map:
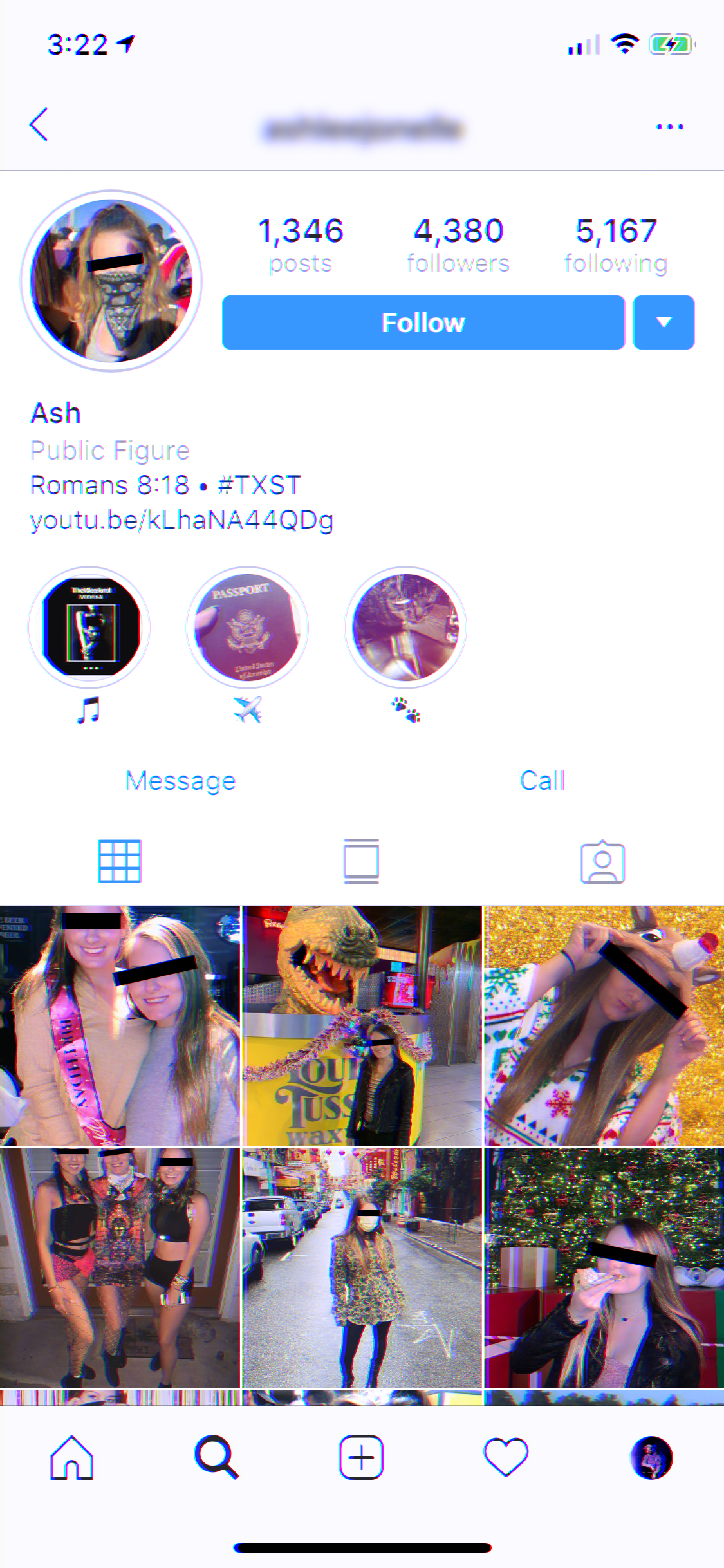
Here is the aforementioned Instagram profile retrieved from the Tinder app on my phone. By their own admission, they are a public figure.
I supplied photos from their Instagram profile to my bot, which was logged in on a different Tinder account. Now, I could test if this new account could independently find the target using only their Instagram photos. This Tinder account used a search radius of 100km in a different city.
we have a winner
Photo 1:
url: https://images-ssl.gotinder.com/5bc8f7dae514cdd93aaf01e8/640x640_ecd59775-db77-4bcd-87b0-4a58a5bad23e.jpg
MSE: 640.716196813
SSIM: 0.608535287135
bits of difference: 8
facial distance: 0.158342834194Photo 3:
url: https://images-ssl.gotinder.com/5bc8f7dae514cdd93aaf01e8/640x640_2d97db2f-ed20-4740-9433-e7be489a3259.jpg
MSE: 1868.14997984
SSIM: 0.476959033051
bits of difference: 16
facial distance: 0.153773397308Photo 2:
url: https://images-ssl.gotinder.com/5bc8f7dae514cdd93aaf01e8/640x640_3cd5ad04-cf49-4a3f-830e-62b54ff30877.jpg
MSE: 319.007284177
SSIM: 0.810429765793
bits of difference: 4
facial distance: -1Photo 4:
url: https://images-ssl.gotinder.com/5bc8f7dae514cdd93aaf01e8/640x640_5bd64ff2-a680-4a90-b48e-6f5d1efdf1e1.jpg
MSE: 1576.16420581
SSIM: 0.542256904314
bits of difference: 72
facial distance: -1Now that this janky program has proven to be pretty effective, I’ve been reevaluating the amount of information I want to put on social media. What kind of information could people get if they really worked hard at it? We’ve seen how companies are starting to give out what you thought was your personal data, like your private messages, friends lists, or search habits. In fact, let’s play a thought experiment with that…
Expanding
There are several ways I could take this program in the future if I wanted to exploit Tinder even more in it’s current state.
Triangulation
The easiest to exploit datapoint would be distance from the user to the bot, which Tinder readily provides. Using a network of Tinder bots working in at least three different locations, it would be easy to use the same kind of triangulation that finds earthquake epicenters:
Epicenter Triangulation
We can make the distance to the target from each bot the radius of a circle centered at that bot. In this example, the centers would be Elko, Eureka, and Las Vegas. Because the radius is the distance from the user to the bot account, the point where the circles all intersect is where the target is located.
Profile Hashing
Having to dislike all of the users is a pain, because they end up getting clogged in the program’s search, and Tinder starts showing me fewer and fewer new users. A solution is to build a function that indexed users to a database using their facial data or their image hash as the bot scanned Tinder. Target images could be used to search the database much faster, which could quickly return conclusive results as to if the user existed in the database or not. The bot network on Tinder would be used to solely to upload new accounts to the database for searching. With the infrastructure in place, I could purchase a premium Tinder Gold Membership™ and with my unlimited likes, I could fill up my database. At this point, I would have lived long enough to see myself become the villain.
Concluding
I hope that the point I’m trying to prove with this exploit is now much more evident. In this rat race to make a profitable social media service, companies don’t consider security a top priority. They can’t even get their messaging straight. Without considering security, the program I’ve written easily demonstrates just how easy it is to use all of your public data against you, using the mechanics constructed by the company. Even if the data you are putting out is benign on the surface, the mere existence can be used against you.
Be aware of this when using services like Tinder. This kind of functionality is all within the parameters of Tinder’s functions. I’m not stealing data, I’m not hacking into their servers, I’m not doing anything particularly illegal. I’m just automating a specific function on their app.